Attackers use many techniques to access user credentials. They can purchase valid username and password combinations on the dark web to access active accounts at various financial institutions. These bad actors use automated tools to quickly test thousands of customer login details across multiple targeted organizations to see if any of them work. One main reason why they're successful is that many people use the same username/password combination for multiple accounts. One survey of cybersecurity executives showed 24% admit to reusing passwords despite their own policies against the practice.
Those odds against success may seem high, but if an attacker steals 10,000 credentials, they can take over around 10 valid customer accounts. Once they gain access, they can change username/password combinations and start to execute their mission. That can include transferring or withdrawing funds, applying for loan applications, or conducting credit card fraud. In the last five years, targeted attacks have impacted more than one billion user accounts.
 PayPal
PayPalIn 2023, PayPal announced in a security incident notice that threat actors gained access to 34,942 PayPal accounts. In an official statement, PayPal asserted that no financial information was accessed and payment systems were not affected. Many experts weighed in on the incident saying that users likely fell victim to the attack due to password reuse.[2]
 Nintendo
NintendoNintendo announced in 2020 that approximately 300,000 accounts were compromised through unauthorized logins. The company said users' credit card information was not exposed; however, a fraction of the breached accounts were used to make fraudulent purchases.

Legacy security technologies may not immediately generate meaningful alerts indicating any unusual activity that would suggest malicious behaviors. That is why detecting and mitigating these attacks is difficult. Most security technologies are ineffective against behavioral-based attacks, such as unauthorized users leveraging stolen credentials.
Read More: Detecting Compromised Credential Attacks

Many companies also do not have the time or resources to handle compromised credential attacks on a large scale or high level of sophistication. Only 38% of organizations said their security team was sufficiently staffed, according to IBM's 2022 Cost of a Data Breach report.
Attacks using compromised credentials often leave very few traces, if any. When hackers gain access to a legitimate user's login credentials, they become invisible to most detection solutions. SIEM 1.0 platforms are most effective in detecting malicious content associated with external threats, not malicious behaviors from internal ones. The same goes for many enterprise-level firewalls and endpoint solutions.
Data breaches caused by compromised credential attacks had the longest lifecycle.
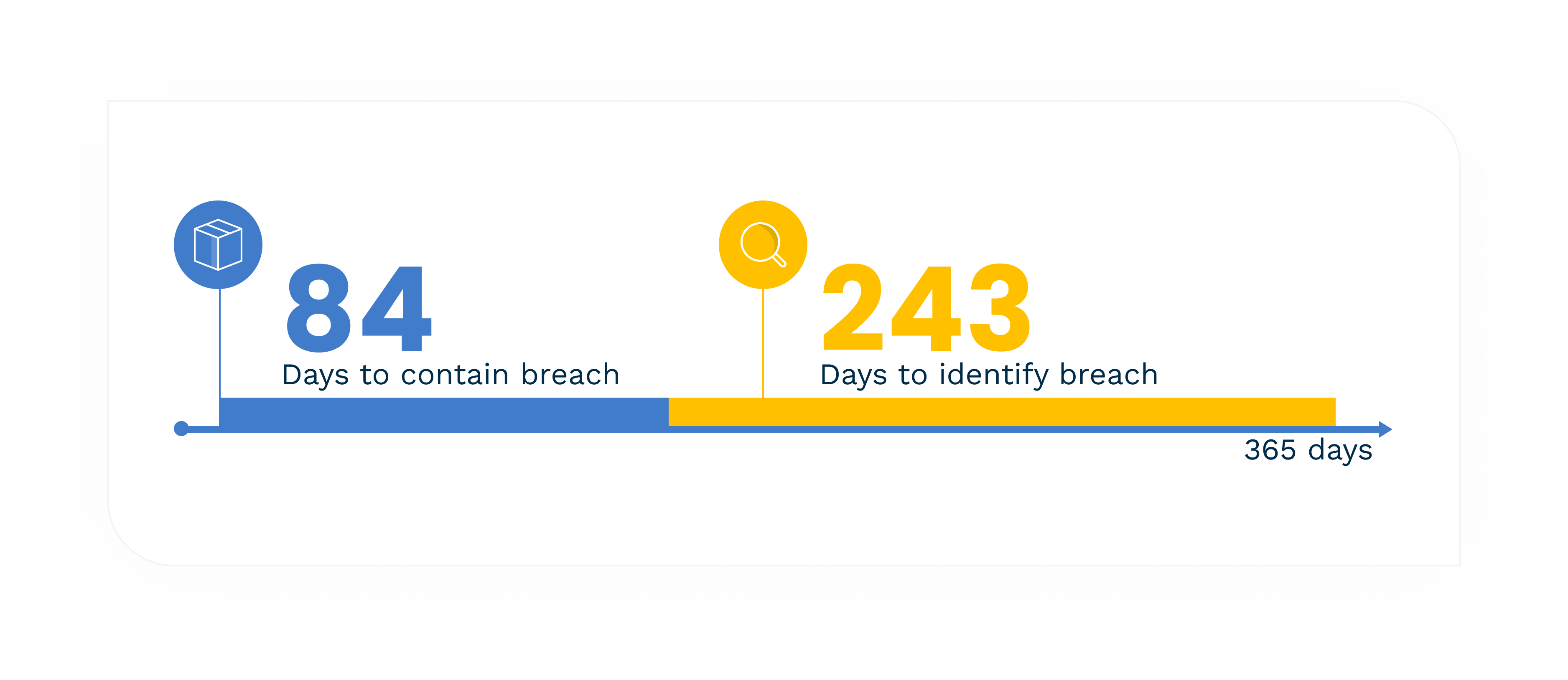
That time is 16.6% longer than the overall average time to identify and contain a data breach.[3]
The financial impact of a data breach can cripple an organization. The average cost to an organization hit by a data breach caused by a compromised credential attack is $4.5 million. The cost to remediate attacks is more than $800,000.
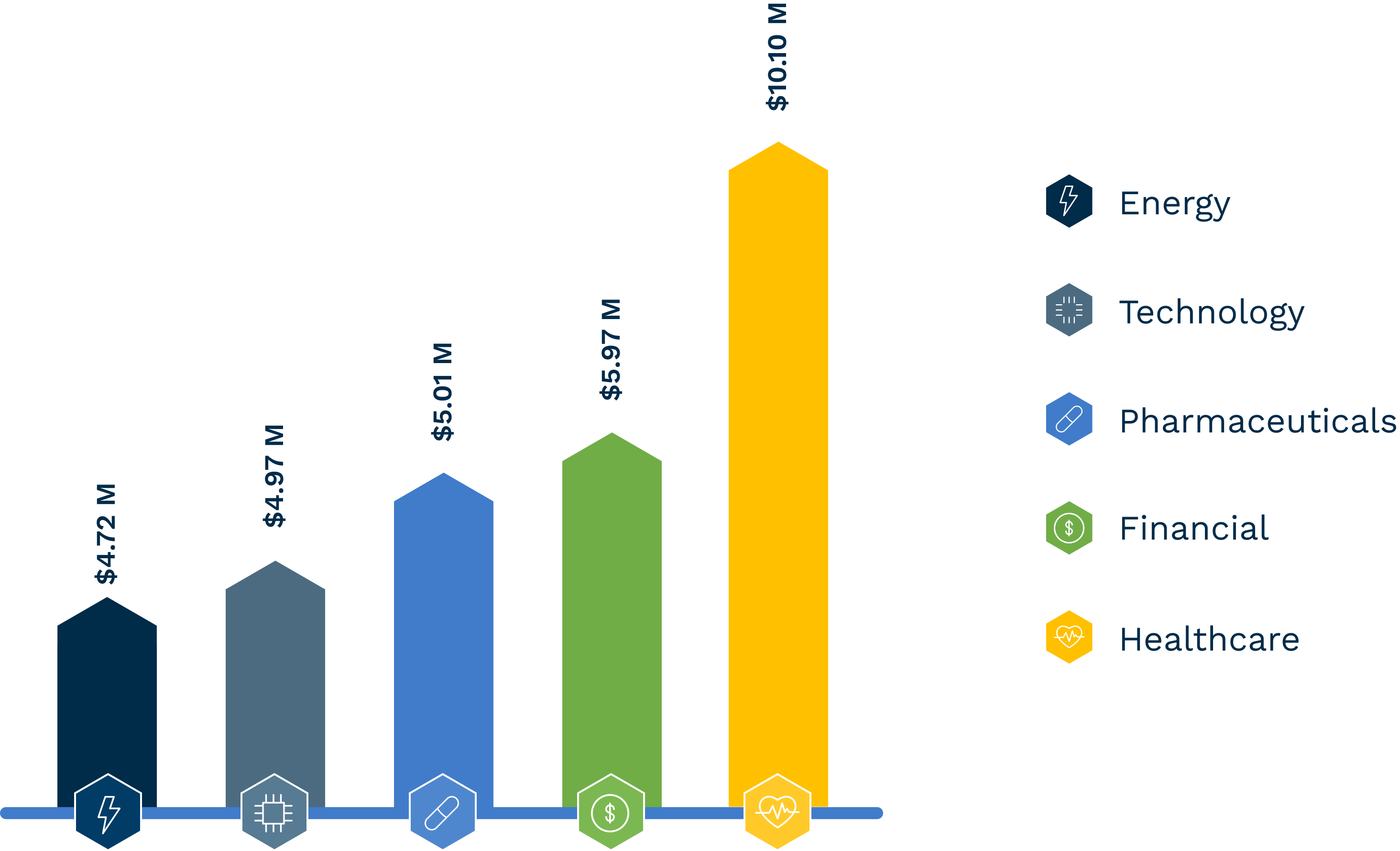
The financial industry is considered a high data protection regulatory environment. Breaches in those environments tend to see costs accrue for years following the breach. An average of 24% of data breach costs were accrued more than two years after the breach occurred.[4] Regulatory and legal costs contribute to the longevity of the impact.
The global financial sector is one of the biggest cybercrime targets in the world. As attackers become more sophisticated, the volume and complexity of the attacks go up, threatening a company's finances and operations.

Every organization wants a bulletproof solution to prevent cyber attacks from bad actors. The truth is, it is not possible to guarantee with 100% certainty that a sophisticated attacker will never find a way to access your system. Some attacks cannot be realistically prevented. However, companies can develop a multi-layered security posture that can accelerate the detection and mitigation of the attack to minimize the damage attackers can cause.
Read More: Early Detection and Response Is Crucial

Many operating systems, databases, and software solutions have preinstalled login credentials. Default credentials are a consistent source of security risks and have been for decades. Systems administrators must have visibility into systems running with default credentials and be able to update them as needed. This task can be challenging in a large organization but it's an easy win in the fight against cyber attacks.
Using tools such as Multi-Factor Authentication (MFA) and CAPTCHA can help reduce the risk of a credential compromise attack. However, hackers have found creative ways to overcome these obstacles and still gain access to user accounts. The best defense is to employ tools that allow security teams to establish baselines for normal user behaviors, then quickly identify any anomalies that indicate possible malicious behaviors. A next-generation security information and event management (SIEM) platform that leverages user and entity behavior analytics (UEBA) can help organizations identify these anomalies and stop attacks.
One example is Exabeam. It is a powerful SIEM platform that allows analysts to detect and mitigate a wide range of threats. It can identify external threats like malware-based ransomware attacks, as well as internal behavior-based threats like compromised accounts and malicious insiders.
Read More: Use Context to Craft Custom Rules That Improve Exabeam Performance
Exabeam works best when it is customized to fit the unique risk profile of the organization it protects. Custom rules allow analysts to dramatically reduce enterprise risk by targeting high-risk vulnerabilities specific to their IT environment.
The most advanced SIEM platform is only as effective as the information security team that manages it. Unfortunately, scaling an in-house team can quickly become cost-prohibitive, and skilled talent is hard to find. A growing number of organizations now outsource SIEM management and MDR services because it allows them to scale efficiently and offers the best protection for their networks.

Lumifi is a managed detection and response provider with 24/7 SOC monitoring capabilities and a staff of highly specialized security experts.
Lumifi has deployed SIEM platforms in over 2,000 organizations globally. Lumifi has been successfully using Exabeam Fusion SIEM for several years, for both our clients and ourselves.
Read More: Pros and Cons of Lumifi Services vs. One Full-Time Employee
Our knowledge of evolving threats based on malicious content and malicious behavior allows us to respond faster and more decisively to new threats as they emerge.
Talk with a Lumifi cybersecurity expert today.
[1] https://www.cloudflare.com/learning/bots/what-is-credential-stuffing/
[2] https://thecyberwire.com/stories/f2f865b1b261486c94af07d020a36fa2/paypal-user-data-compromised-in-credential-stuffing-incident
[3] https://www.ibm.com/downloads/cas/3R8N1DZJ
[4] https://www.ibm.com/downloads/cas/3R8N1DZJ
